Obtaining assurance on the security of your CDR data environment.
With CDR going live on 1 July 2020, Accredited Data Recipient (ADR) applicants must demonstrate the security effectiveness of their people, processes and technology. The key is to demonstrate security, whilst minimising the cost.
What security controls are needed?
The Consumer Data Right rules require an organisation applying to become an ADR to meet minimum requirements for protecting CDR data from two broad types of risk:
- (a) misuse, interference, and loss, and;
- (b) unauthorised access, modification, or disclosure.
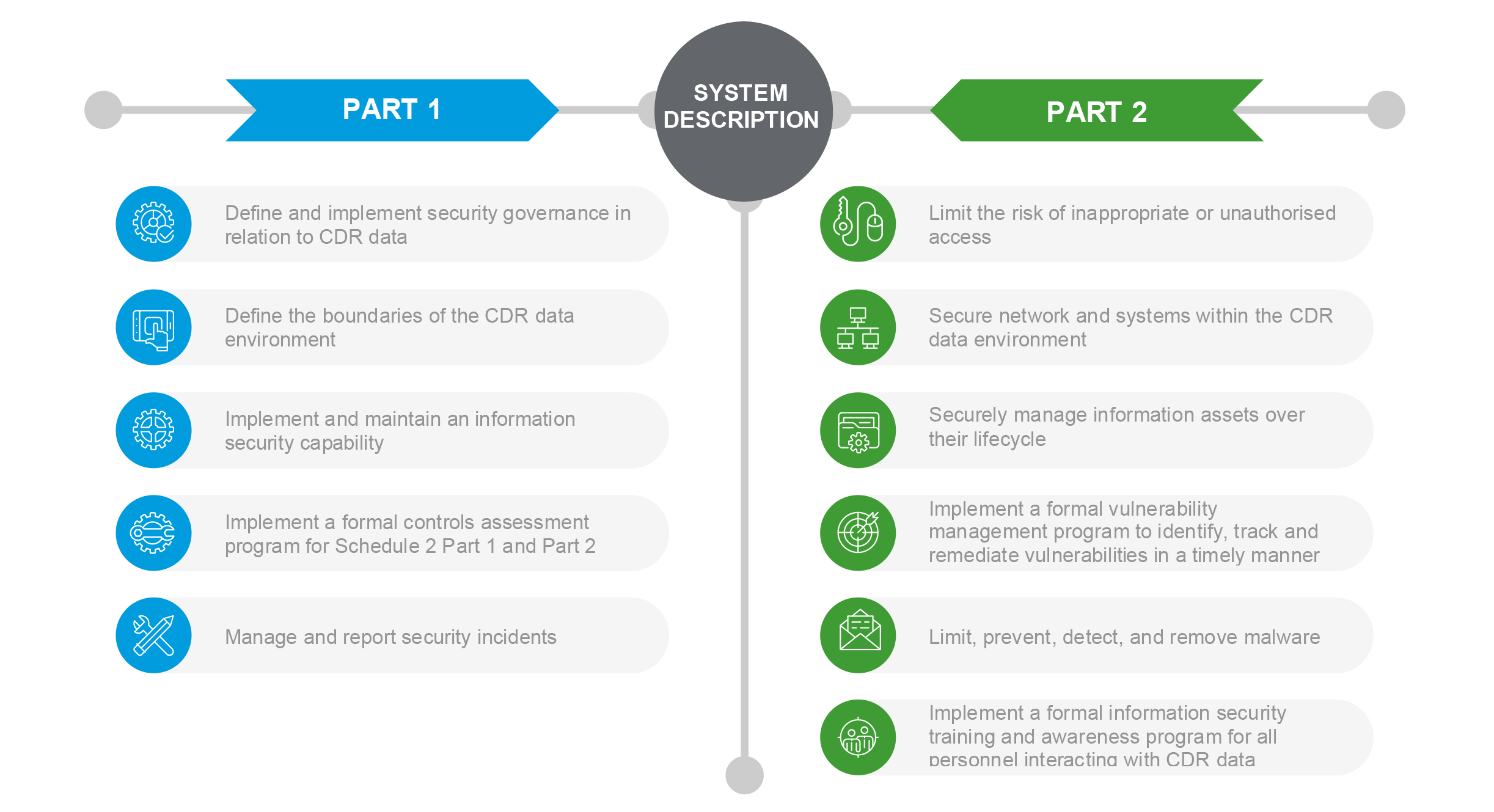
The CDR rules outline the controls required to manage these risks in Schedule 2 Part 1 (security governance) and Schedule 2 Part 2 (minimum control requirements).
The CDR rules also require an applicant to document their data environment (the people, processes and technology) in a comprehensive system description.
The more difficult control requirements relate to implementing application whitelisting, data loss prevention and server hardening to accepted industry standards
What is required when applying for an accreditation?
To become an ADR, an organisation needs to demonstrate that they have effectively designed security controls and implemented those controls as designed.
For a nonauthorised deposit-taking institution (non-ADI), this requires a “Type I” reasonable assurance report in accordance with the Standard on Assurance Engagements ASAE 3150 – Assurance Engagements on Controls, or accepted comparable standards, as identified by the ACCC in the ‘CDR - Supplementary accreditation guidelines information security’.
A "Type I" provides assurance on the design and implementation of controls at a date or point in time.
In Australia, these reports can only be prepared by an independent registered auditing firm (CAANZ or CPA) and only a suitably experienced, qualified and independent individual can sign the report as the lead information security assurance practitioner.
Lessons from previous CDR information security accreditations
Work with a partner who has done it before to effectively translate the CDR Rules. The information security obligation under CDR Rules is broad whilst also containing CDR-specific control expectations. The complexity of the compliance criteria requires a thoughtful discussion to clarify what is expected. Each minimum control requirement contains multiple controls and the mapping to ISO 27001, SOC 2 Trust Services Criteria, and PCI DSS contained in the ‘CDR - Accreditation controls guidance’ workbook, is incomplete.
Options for reducing the scope of your CDR data environment include network segmentation, tokenisation, de-identification, anonymisation, and pseudonymisation.
This process can be complex, expensive and reduce the effectiveness of your business case for accreditation, so they need to be carefully considered.
Continue reading the full article below.