Imagine it’s Black Friday. Your systems are at full capacity, and suddenly a threat actor breaches your network, silently exfiltrating sensitive data. Your cybersecurity and IT teams spring into action, racing to contain the damage and investigate the source. In the chaos, a few pressing questions emerge:
- How did this happen?
- What vulnerabilities were exploited?
- Have we done enough to manage our cybersecurity risks?
Scenarios like this are no longer hypothetical. According to IBM’s 2024 Cost of a Data Breach report, the average cost of a breach surged to USD 4.88 million, up from USD 4.45 million in 2023. The report also highlights that breaches involving stolen or compromised credentials took 292 days on average to detect and contain—the longest of any attack vector.
The Global Cybersecurity Outlook 2025, released by the World Economic Forum in collaboration with Accenture, further underscores the increasingly complex threat landscape organizations are navigating.
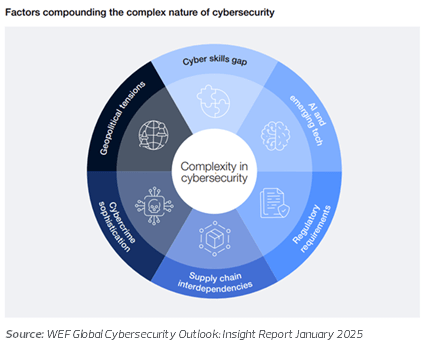
The Critical Question: How Should Organizations Respond?
There is no one-size-fits-all answer to this question. Every organization faces unique threats, operates under different constraints, and has its own risk appetite. But one thing remains consistent: the need to understand your cybersecurity maturity level and align it with your business strategy.
That’s where the NIST Cybersecurity Framework (CSF) 2.0 comes into play. As a globally recognized framework, it offers practical guidance to assess and improve an organization’s cybersecurity risk management in a structured, scalable way.
Understanding the Four Tiers of Cybersecurity Maturity
NIST CSF 2.0 defines four Cybersecurity Maturity Tiers, each reflecting an organization's level of cybersecurity governance and operational capability:
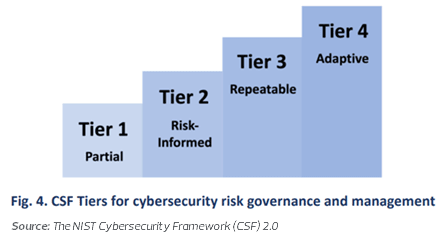
1. Tier 1 – Partial: Cybersecurity efforts are ad hoc and largely reactive.
2. Tier 2 – Risk-Informed: There is some awareness of cybersecurity risks, but practices are not
consistently applied across the organization.
3. Tier 3 – Repeatable: Policies and processes are established and executed consistently across the enterprise.
4. Tier 4 – Adaptive: The organization proactively adapts to changing threats through continuous improvement and learning.
Cybersecurity is a Journey (Not a Destination)
Building cyber resilience is not a one-time project. It requires ongoing improvement. Here’s how organizations can navigate the maturity journey:
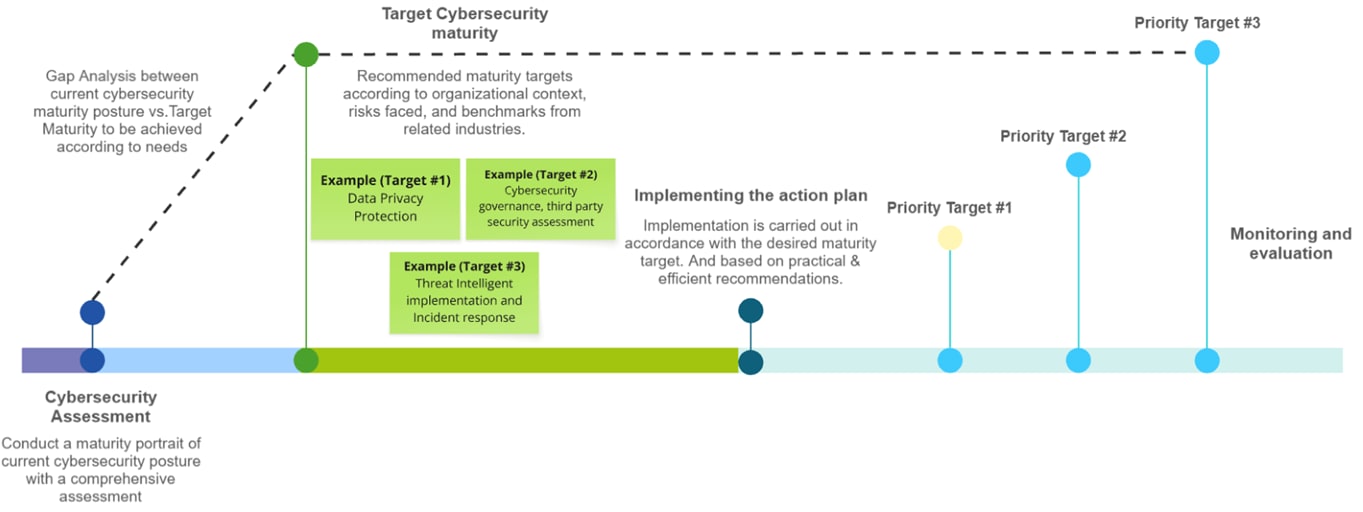
- Assess Current Cybersecurity Maturity
Identify existing controls, policies, roles, and practices. Map these against the six CSF Functions (Identify, Protect, Detect, Respond, Recover, and Govern) and determine your current implementation tier. - Define the Target Profile
Set clear goals for where your organization wants to be in terms of cybersecurity capabilities, aligned with your business needs and risk tolerance. - Conduct Gap Analysis & Prioritize Actions
Compare your current and target profiles to identify the gaps. Prioritize initiatives based on risk exposure, business impact, and feasibility. - Develop a Roadmap & Implement Improvements
Build a cybersecurity roadmap outlining short-, mid-, and long-term initiatives. Execute improvements with stakeholder alignment and commit to ongoing monitoring and refinement.
Regulatory Drivers in Indonesia: Why Cybersecurity Maturity Matters Now More Than Ever
Indonesia’s regulatory landscape has raised the bar for cyber resilience, especially in the financial sector.
Peraturan Otoritas Jasa Keuangan Republik Indonesia Nomor 11/POJK.03/2022 and Surat Edaran Otoritas Jasa Keuangan Republik Indonesia Nomor 29/SEOJK.03/2022
This regulation from the Financial Services Authority (OJK) emphasizes the need for banks to assess their cybersecurity maturity, including:
- Mandatory evaluation of IT governance, risk, and security posture.
- Implementation of Three Lines of Defense and periodic assessment of cyber resilience.
- Integration of cybersecurity maturity assessments into internal audit and risk monitoring processes.
Peraturan Bank Indonesia Nomor 2 Tahun 2024
Bank Indonesia’s latest regulation outlines minimum standards for cyber resilience:
- Institutions must perform self-assessments of cybersecurity maturity using recognized frameworks (e.g., NIST, COBIT).
- Requirements to demonstrate continuous improvement and incident handling readiness through simulations and controls.
- Strong emphasis on Board involvement, cyber governance, and threat intelligence capabilities.
- Buy-in from senior leadership and operational teams.
What You Can Get from a Cybersecurity Maturity Assessment
By conducting a cybersecurity maturity assessment using the NIST Cybersecurity Framework (CSF) 2.0, your organization can gain:
- A clear view of current maturity across functions
- Alignment between cybersecurity and business objectives
- A realistic, phased improvement roadmap.
This assessment not only identified gaps but also catalyzed cultural and procedural shifts toward more proactive cybersecurity governance.
Key Takeaways
- Cybersecurity incidents are costly and growing in complexity. Maturity assessments provide clarity and focus.
- NIST CSF 2.0 offers a flexible, structured model to guide cybersecurity improvement.
- Cybersecurity is a continuous process, not a project. Regular reviews and updates are essential.
- Indonesian regulators now expect financial institutions to actively assess and improve cyber maturity.
By Erikman D Pardamean & Dena Sucianandika, Technology Risk Consulting Practice


