Your Trusted Partner in Cybersecurity, Compliance and Resilience
In today’s hyper-connected digital landscape, cybersecurity is no longer a technical afterthought, it is a strategic imperative. With the increase in cyber threats, evolving regulations and growing complexity of digital operations, organizations must take immediate, proactive action to protect their assets and maintain trust.
We work along with our clients to turn cybersecurity into competitive advantage. With our global cybersecurity expertise and understanding of the local business environment for the last 6 decades, we provide cyber solutions for business navigating today’s digital threats.
At RSM in Kuwait, we collaborate with you to embed cybersecurity into every layer of your organization, protecting what matters and powering growth in a connected world.
We enable your business to operate securely, innovate boldly and lead confidently in a digital-first landscape. Our approach enables you to manage digital risks, protect assets and safeguard trust in an evolving compliance and cybersecurity threat landscape.
.jpg)
Cybersecurity Consulting Services Overview
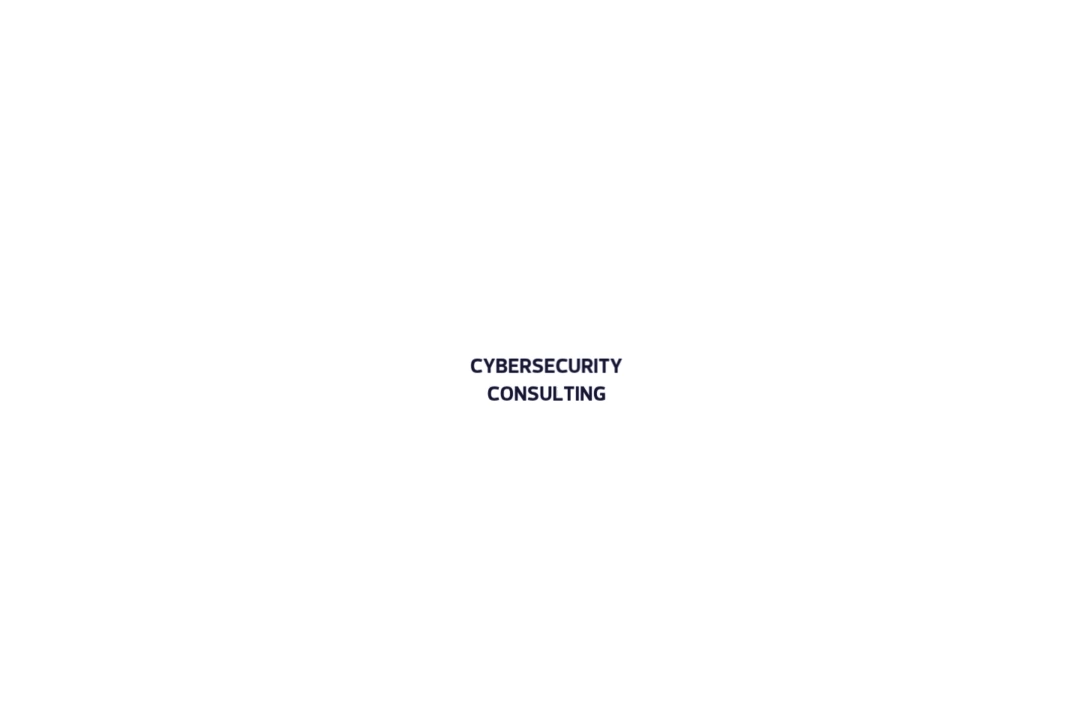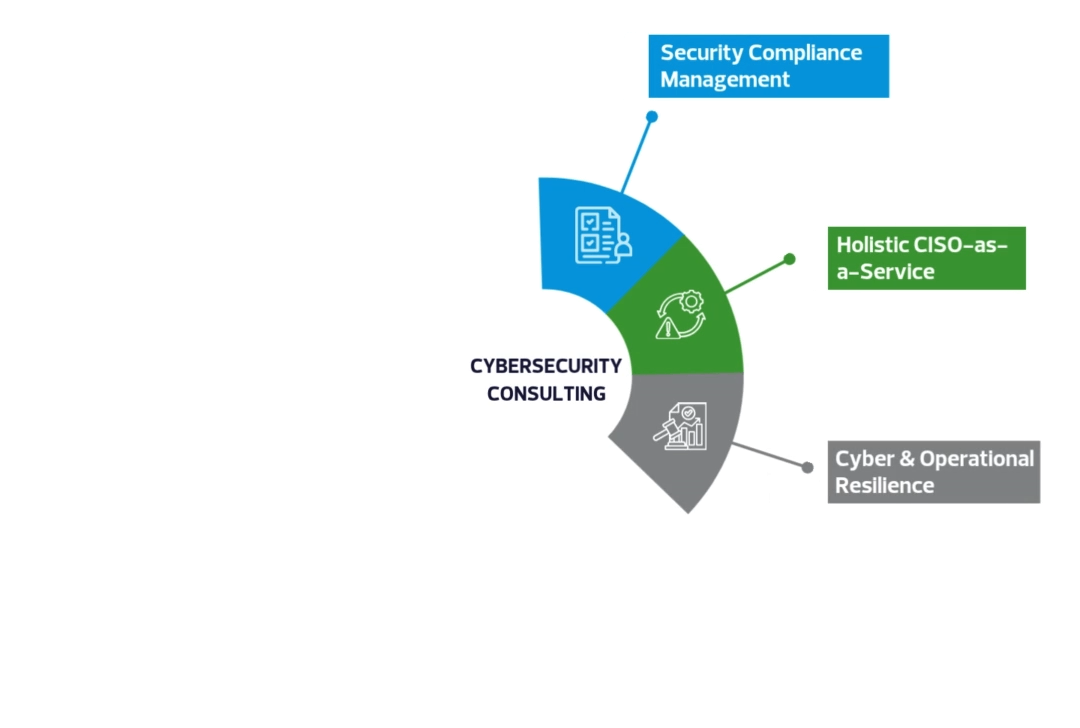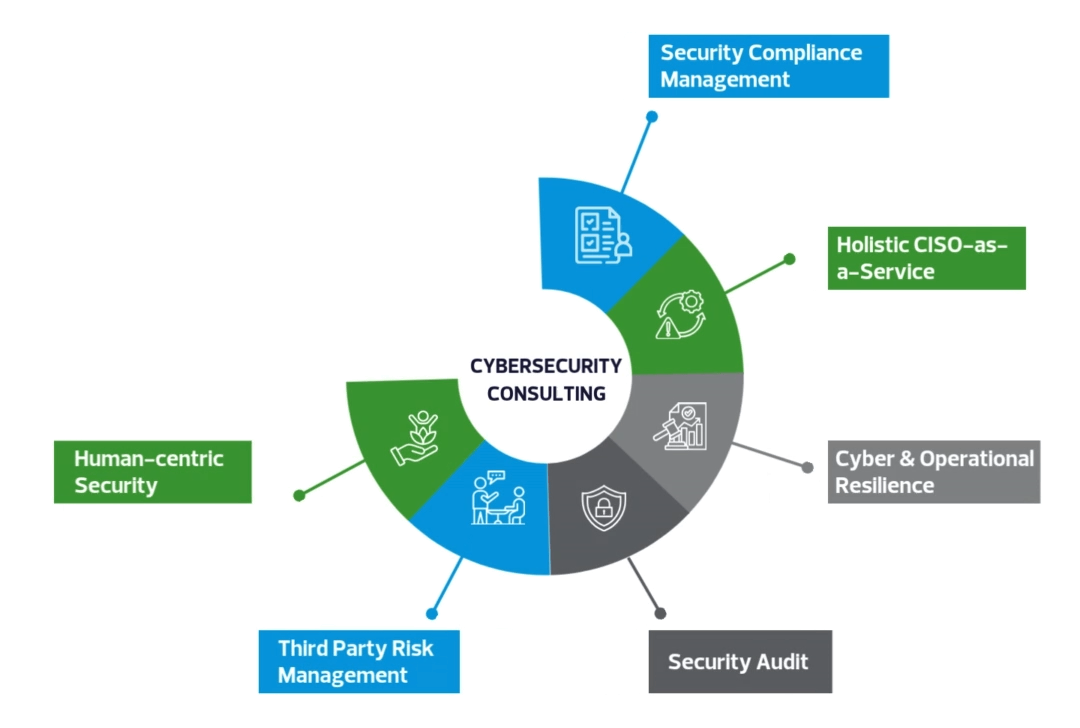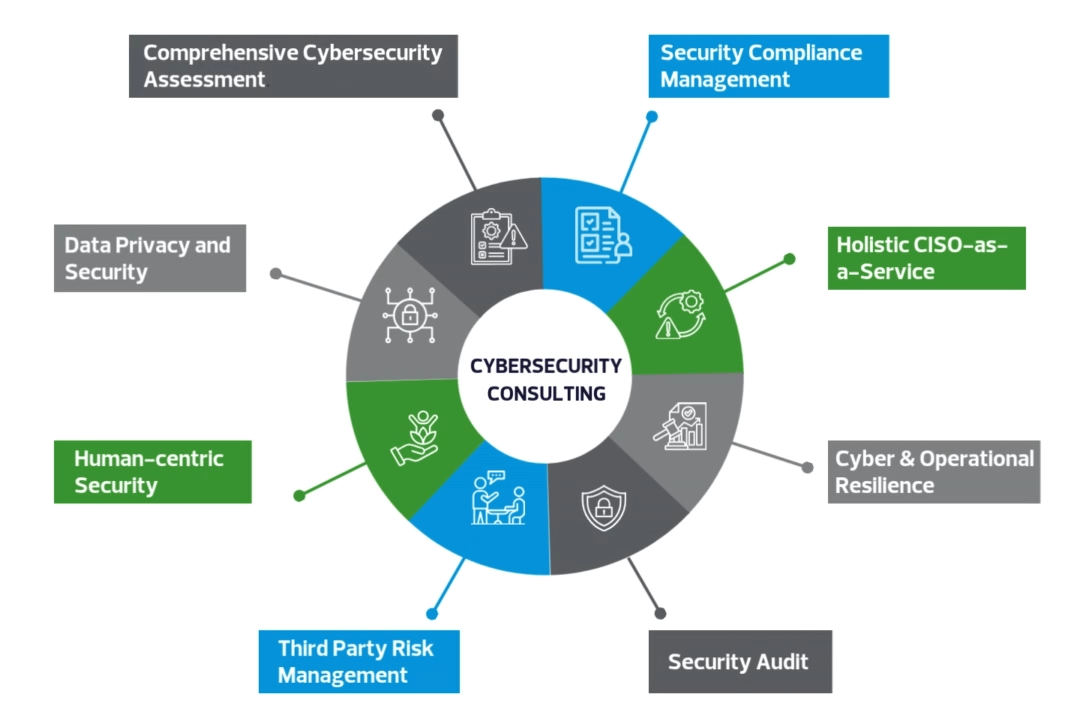
- Comprehensive cybersecurity assessment
- Central Bank of Kuwait - cybersecurity and operational resilience framework readiness
- Security policies and procedure development and Implementation support
- Pre-certification readiness of ISO 27001
- Conducting security risk assessment
- NIST standard readiness
- Privacy management framework establishment
- Conducting privacy Impact assessment
- Cybersecurity officer as a service
- Cybersecurity consultant as a service
- Security program manager as a service
- Security training and awareness
- Pre-certification readiness of ISO 22301
- Resilience policy, plans and procedures development
- Conducting BCM exercise and simulations
- Third party risk management framework establishment
- Conducting third party risk assessments
- Conducting IT general control assessment
- Conducting IT application control assessment
- Integrated GRC platform and implemetation support
- Others
Why Choose RSM in Kuwait for Cybersecurity Consulting?
Value Advantage
We offer transparency and align resources
based on your needs, enhancing value for your investment
Gain Competitive Advantage
Helps position your organization as a secure
and steady business partner
Reduce Security Risk
Reduces the likelihood and impact of data
breaches, ransomware, third party risks,
and operational disruptions
Compliance Assurance
Reduces the risk of costly fines, legal actions
and reputational damage from compliance
breaches
Improved Cyber & Operational Resilience
Making your organization more attractive to
partners, investors and customers
Reduce Human-Centric Risk
Build a security-first culture across the
organization, empowering employees as
the first line of defense
Audit Readiness
Prepares organizations for cybersecurity
audits and assessments, simplifying reporting
and documentation for stakeholders and
regulators
Actionable Insights
Receive actionable insights that enable
leadership to make informed, strategic
decisions regarding cyber risk
Meet Our Expert: Whom You Can Trust
At RSM in Kuwait, our cybersecurity consulting practice is led by our seasoned partner who blends global expertise with a deep understanding of the local threat landscape. Their leadership works to make every cybersecurity strategy proactive, evidence-based and focused on safeguarding your business against evolving cyber threats.

Bhaskar Maheshwari
Bhaskar leads our cybersecurity consulting services with 18+ years of global experience delivering complex consulting engagements and building high-performing security teams. He has served clients in banking and financial services, technology, telecommunications, pharmaceuticals and energy sectors across the US, UK, EU, GCC and APAC.
Credentials: BE, MBA,CISA, CISM, PMP, TOGAF, ITIL Expert, MBCI, COBIT-F














