When it comes to cybersecurity, the lack of confidence from businesses is understandable because the reality today is that the threats are greater than protection - the hacker is always two steps ahead.
Not only are there more hackers, but we have seen a move towards syndicates where criminal organisations across the globe are joining forces - often working together via the dark web quite often geopolitically - making the threat stronger.
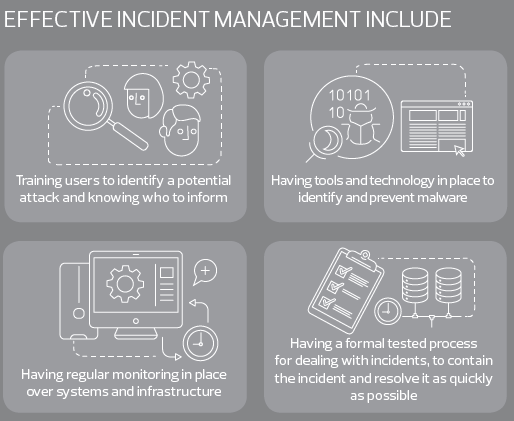
Doing nothing is not an option. The first step to protection is understanding that investing in security tools and technology will not necessarily prevent an attack, but with strong user education and awareness, it may help you to monitor, detect early, and quickly deal with a breach should one occur.
A strong incident management process will also be crucial to containment. The more equipped you are to contain a potential breach, the less you are you going to be impacted from it - whether that be reputationally or financially.
Controls to prevent, detect, contain and build reliance can be the difference between little impact and a public scandal with significant financial loss.
If you want to keep pace with the developments in technology, you need to keep pace with the developments in cybersecurity - the two must go hand in hand.
The 64% who believe they have unknowingly been breached is a major concern given the implications and this indicates the psychological stronghold business leaders are under by cyber attackers.
We have seen instances where, via phishing, an attacker has dropped malware into the back of an email inbox and over time all email traffic to and from that email address was redirected to an email inbox abroad, and this went on for months without being detected. An investment in monitoring tools could have detected this but as with many of the clients we see, the damage had been done before they came to us for advice.
Cybersecurity needs to be a priority before the breach as well as during the breach, as mitigation work whilst the breach is occurring can make a huge difference on the potentially damaging effects. Prioritising cybersecurity after breach is, by definition, too late.
