What types of businesses have you seen attacked in your market?
Sheila Pancholi, Partner – RSM UK
The world is moving on quickly. Smart devices and social media are intertwined, leaving users, homes, healthcare, financial, manufacturing and other industries vulnerable, hackable and easy targets to be taken down and/or held for ransom. The numbers are getting too large to ignore, and the steps manufacturers, companies, and consumers are taking to secure us all are too slow and too few. Many of these companies are themselves suffering from cybersecurity budget cuts along with skilled security staff shortages.
Phishing, whaling (both types of social engineering) and ransomware still continue to lead as the most popular and successful methods used to gain access to networks, systems and data or gain confidential information. Phishing and whaling techniques can often be deployed on the phone or via texts, they don’t always occur via an email scam.
The UK was the biggest target for ransomware attacks, over the first half of 2019, with the number rising 195% from prior year. In 2019 the US and the UK were still the most attacked nations, positioned first and second respectively.
Darren Booth, Partner - RSM Australia
The weakest link still seems to be through employees and getting them to open malicious emails or click on malicious links. The problem is that many organisations still have legacy systems that are not being appropriately updated and supported, giving attackers an easier attack vector to get a foothold in the organisation once they gain access via an unsuspecting employee.
Gregor Strobl, Partner – RSM Germany
Cyber-attacks have risen to an even higher level of sophistication and hacker groups are using long term tactics and different levels of attack approaches to gain access to the IT infrastructure. This could be the usage of a so-called “guerrilla tactic” where the group would perform a “shadow attack” in order to create chaos and confusion while running around and starting the actual attack.
In addition, it is the pure number of growing attacks that is also proving a greater risk to all companies. The reason for this increase is the high volume of Emotet malware campaigns globally, but also in Germany. According to BSI, Emotet is one of today's most dangerous and widespread malwares. Security researchers first identified the Emotet Virus in 2014. Originally Emotet was designed as a banking malware that attempted to sneak onto your computer and steal sensitive and private information (e.g. by using infected Word Documents). Later versions of the Emotet Virus saw the addition of spamming and malware delivery services. In addition, Emotet is particularly dangerous because it allows the hacker to “load” further malware to the infected infrastructure.
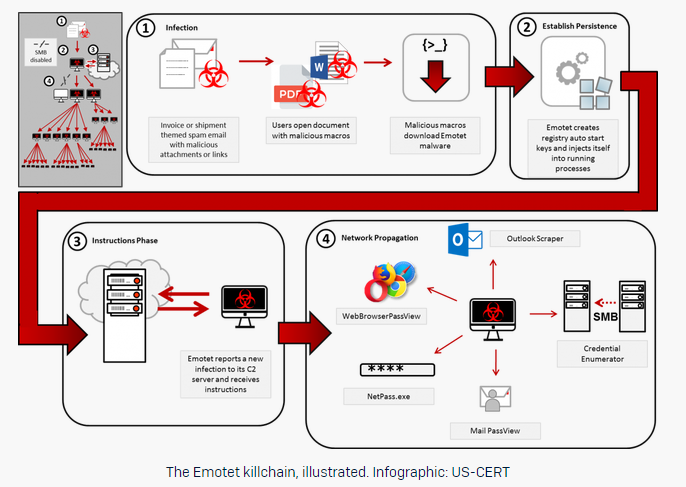
Hope, Kajnalka & Nagy, Lucy, 2019, The Emotet killchain. [Online]. [Accessed 5 March 2020]. Available from: https://news.sophos.com/en-us/2019/03/05/emotet-101-stage-3-the-emotet-executable/




