Data rich IFAs and Wealth Managers have become a target for cyber criminals.
Five contributors to cyber fraud fears
In the ever-evolving cyber landscape, a few ingredients make for a ripe opportunity for the cyber underworld. They include, but of course are not limited to:
- A business economic crisis
- A cost-of-living crisis
- Geopolitical uncertainty
- War and conflict
- A rise in agile working (increasing use of cloud and personal devices)
These ingredients have come together to create the perfect conditions for fraudulent activity and cyber-crime. Businesses are now having to ask themselves the question of ‘when’ they are targeted, no longer ‘if’ they will be.
Organisations are now focusing on protecting their data and, in the event of a compromise, having the right response plan in place to deal with the fall out. Given the intricate web of data held by independent financial advisors (IFAs) and wealth managers, they are a hot target for criminals seeking to exploit weaknesses. It is not just the customer and advisor relationship that criminals are seeking to exploit, but also the other accounts that are interconnected. Many of these firms do not have dedicated teams to protect their information, presenting a potential weakness along any protective cyber chain.
The risk of a cyber-attack is ever present and dynamic in nature as hackers discover new ways of penetrating defences. The extent to which a firm protects its IT infrastructure, systems and data from cyber-attacks through investment in tools, technology and resources is very much dependent on the firm’s risk profile and risk appetite.
Paul O’Leary, Financial Services Technology and Cyber Risk Assurance Partner comments, “cyber criminals prey on IFAs and wealth managers as they know that data governance practices are typically weak, and many are undergoing significant change and transformation. This provides a potent cocktail of opportunity for an attacker.”
How attacks could occur
Many IFAs and wealth managers are on an exciting journey to transform their services and market proposition, including phone and table-based apps allowing quicker onboarding, easier money inflows, access to total wealth statements and wallets, as well as approvals and signatures of key documents. As they grow and evolve – the processes, practices and ways of working need to consider cyber resilience. Cyber incident response exercises allow leadership to know how well prepared an organisation is, as well as how to respond and recover – and sometimes this can be uncomfortable to hear.
Given the common vulnerabilities seen within IFAs and wealth managers, we have outlined below how a cyber-attack could be initiated:
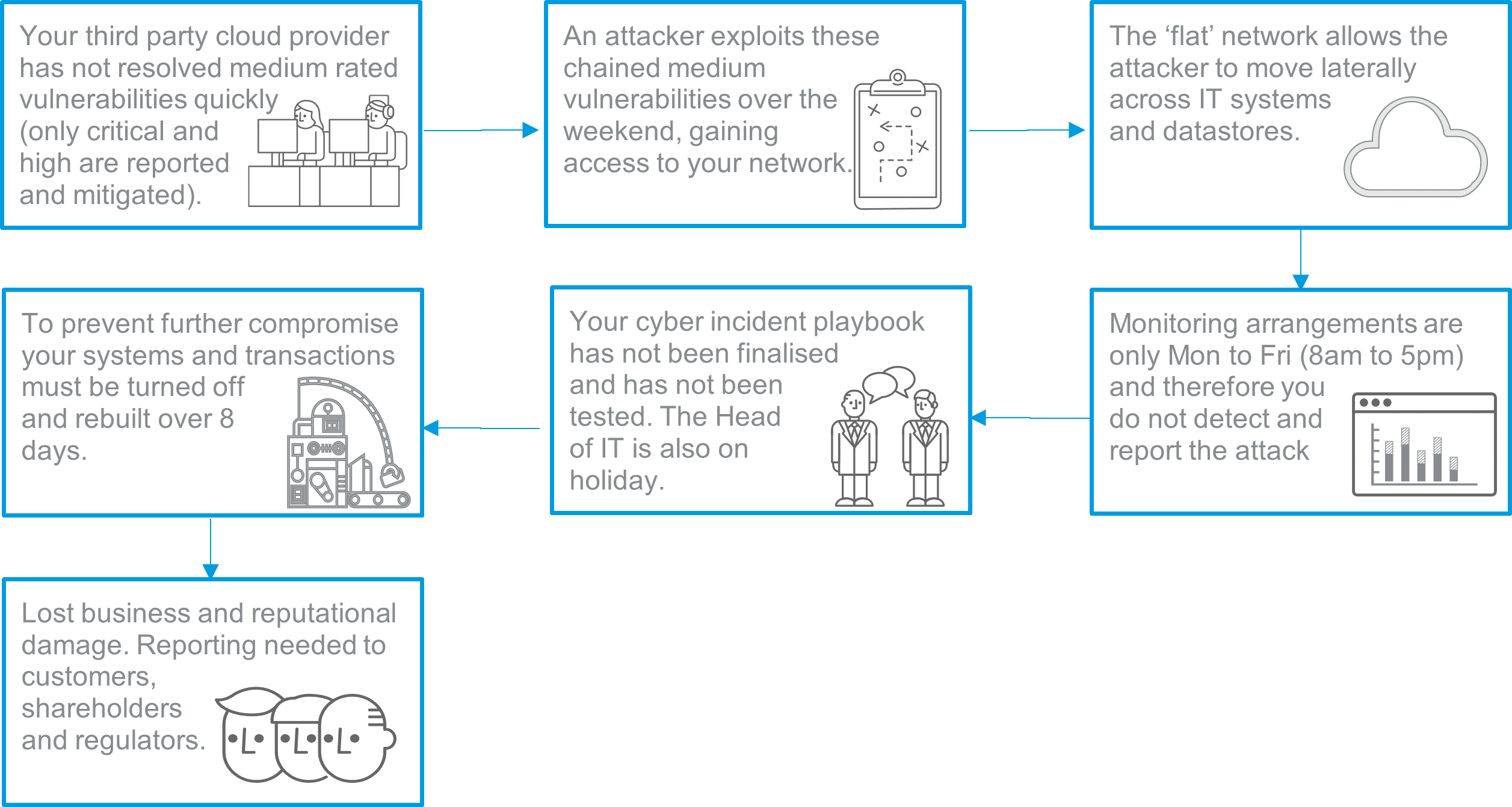
The numbers
There is no doubt that cyber fraud presents an ever-growing threat. According to Action Fraud, the UK’s national reporting centre for fraud and cybercrime for individuals and businesses, there has been a year-on-year increase in both losses, and volume of fraud and cyber-crime reports.
Reports from the National Fraud Intelligence Bureau see hacking making up over three quarters of the reports, followed by viruses, malware and spyware.
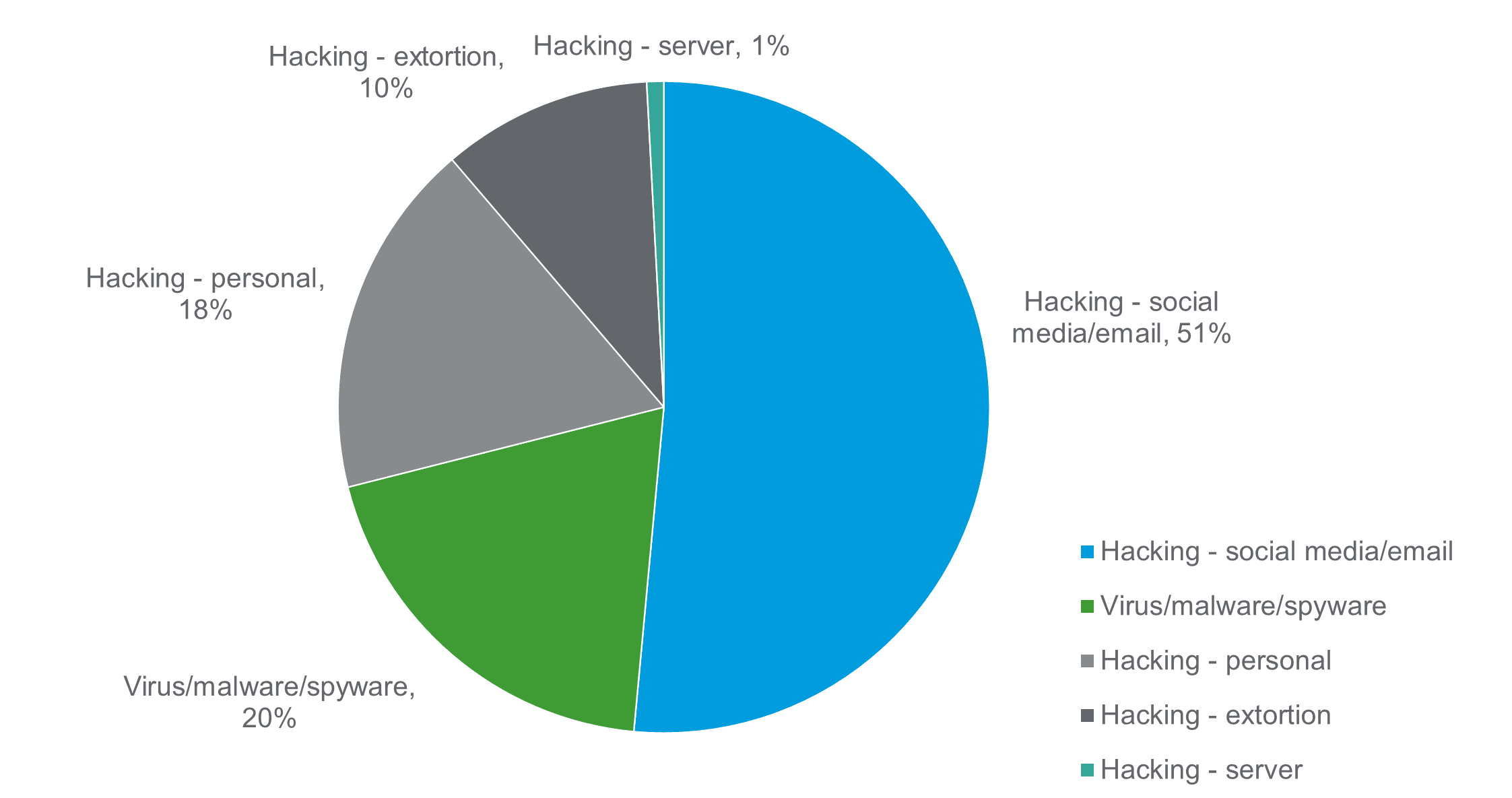 Source: NFIB Dashboard (Public) (arcgis.com)
Source: NFIB Dashboard (Public) (arcgis.com)
The Financial Conduct Authority (FCA) reported a 52% rise in ‘material’ cyber security incidents in 2021. The latest Information Commissioners Office (ICO) data highlights that the most common incidents are ransomware, phishing and personal data sent to incorrect recipients.
There continues to be fear from state sponsored attacks. This is particularly so given the fear of Russian cyber-attacks by way of retaliation to sanctions placed on firms by Western institutions, including financial services. However, there has been a shift in who specifically is carrying out the attacks. The commercial availability of cyber capabilities has provided less savvy cyber criminals with access to sophisticated software, or “hackers for hire”, bought off the shelf.
Sir Jeremy Fleming, who heads the signals intelligence agency GCHQ, said in a speech at the UK’s National Cyber Security Centre: “We’re (. . .) seeing a change in those who can carry out cyber-attacks. This shift leads us to expect that commercial availability of cyber capabilities will increase the future threat to the cyber security of the UK”.
Cyber criminals are using software to spy on systems, waiting patiently for the right moment. This is often achieved from a phishing email or malicious link. When there is a trigger, the software will steal as much data out of the system as possible by way of ransomware attacks. These act very much like hostage situations, but where an organisations data, rather than human individuals, are held at ransom. Criminals use software to gain access into a business’s computer system, it then encrypts the data and files so the business cannot use them. The criminal will then demand payment to regain access.
The National Cyber Security Centre advises firms who find themselves in this situation not to pay the ransom, as there is no guarantee that they will get their locked files or data back, and the money would contribute to the criminal gains.
A recent report suggested that 36% of organisations who paid the ransom went on to be targeted again a second time, 41% failed to recover the data and 43% who paid the ransom still had to rebuild their systems. The challenge for organisations is not only the disruption to business, but also the reputational damage due to this disruption that is much harder to rebuild. Denial of service attacks, which is where the actor floods a server to overload it resulting restricted access, are equally as disruptive.
Five steps to being cyber fraud savvy
Cyber security must be integrated throughout the business, and Boards must have a good understanding all the aspects.
Investing in building robust cyber defences and preparing an effective response for an attack are more effective than the reactive method of paying a ransom and hoping to get the information back. Beyond the software solutions, infrastructure and up to date patching, the simplest approaches are often more effective. Often the greatest vulnerability can be the human operator, so investment in the perfect system alone is not enough. Cyber defence needs to be behavioural too, focusing on that first line of defence. For example:
- Training on cyber risks for staff, with use of ethical phishing exercises, customers and suppliers and empowering the raising of incidents.
- Using different and effective passwords that are regularly changed and using multifactor authentication.
- Clear policies for staff using their own devices for work and remote networks.
- Clear policies for the layperson and a response plan.
- Testing vulnerabilities and dealing with the anomalies.
Each organisation will be on their own digital transformation journey, and cyber security is a fundamental component of this. With 69% of respondents in our recent topical survey suggesting that their digital investments will become more important over the next three years, cyber security should feature heavily in any digital transformation strategy.





