Not a week goes by without news of a prominent organisation falling victim to a cyber attack. This list of organisations seems to grow endlessly as cyber criminals enjoy their successes and try more attacks with newer tactics and techniques.
As the attacks continue seemingly unabated, Boards are asking why? Why are these attacks and their success increasing unabated and more importantly, what needs to change to stem this flow?
The reason for the increase and success of cyber attacks and methods to stall these are really two sides of the same coin. If you scrutinize some of the recent attacks, a common theme emerges – failure in addressing some of the most basic requirements around cyber security. This is not because organisations are ignoring this key business risk, but it is a consequence of not taking a methodical approach to managing this key risk like other business risks.
To revamp how cyber security and risk is managed within organisations, they need to understand and address the six pillars of cyber security and risk management.
Depicted below are the six pillars. I will now discuss these: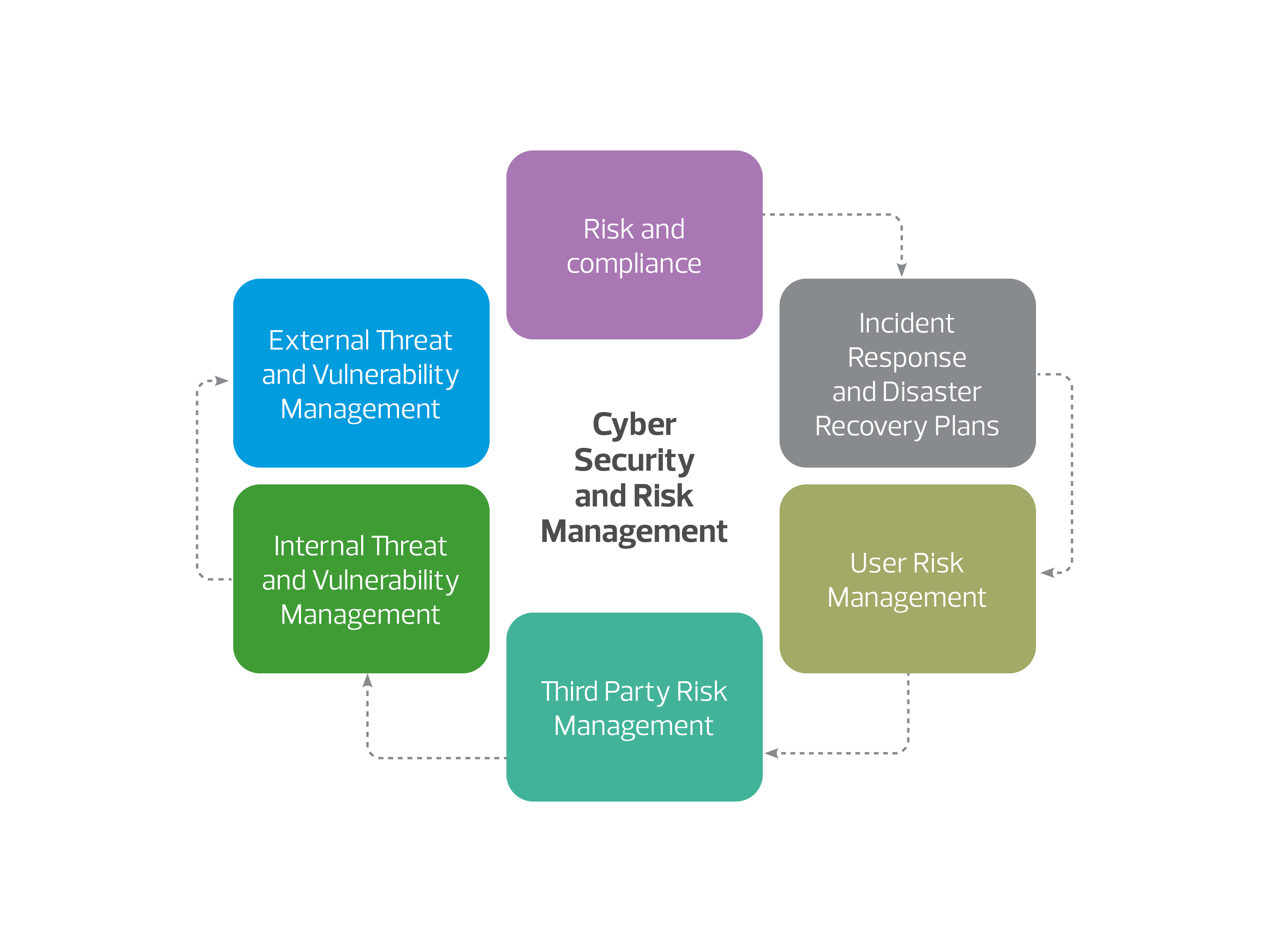
-
Risk and compliance
One of the most fundamental things an organisation needs to do is analyse its cyber risk exposure. This can be easily performed by benchmarking itself against a standard such as ISO27001, NIST-CSF or the CIS Top 18. At a minimum, an organisation needs to assess itself against industry mandates such as APRA’s CPS234 for the Financial sector. This is an essential starting point as unless this process is undertaken, an organisation will not understand its cyber security risk and will struggle to manage them well
-
External threat and vulnerability management
Another important factor is understanding what you look like from the outside to cyber criminals. If you understand this, you can better protect yourself by understanding and remediating any gaps and vulnerabilities in your environment before cyber criminals exploit these. This needs to be a constant effort as new vulnerabilities emerge regularly
-
Internal threat and vulnerability management
This is an important step as well. We are seeing an increase in attacks from the inside either through employees who have trusted access to your environment or an attacker who may have surreptitiously obtained a user’s credentials via a phishing attack. Either way, this represents an internal risk to your organisation that you must manage. Again, understand what your environment looks like from the inside to those with nefarious intent. Understand what vulnerabilities exist and focus on remediating these. This needs to be a constant effort due to new vulnerabilities emerging regularly. Concepts such as Zero Trust and user behaviour analysis are important controls to help address these types of vulnerabilities
-
Third party risk management
By now everyone is familiar with the Solarwinds breach. Solarwinds is a popular IT management tool that was breached and then this breach was used to attack a multitude of Solarwinds clients globally. This is a particularly debilitating type of attack as organisations usually give trusted access to third party suppliers. It is this very trust that is getting exploited by cyber criminals. It is important to thoroughly assess your third-party suppliers before engaging with them. Even after the initial engagement, this assessment should be performed at least yearly so that you understand your vulnerabilities at this layer and can address these before it becomes a security incident. What is key is to understand the impact of a third party breach on you and not a generic score on the third-party vendor so you can understand this impact and be able to make decisions on how to mitigate or avoid this risk by not engaging with the third party
-
User risk management
Users can be your greatest security asset or your biggest vulnerability depending on the cyber security education and training you provide to them. If a user is well educated on spotting a phishing email, they are less likely to fall for one. However, if they have not been trained, then any enticing phishing email may cause them to click on a malicious link and provide a cyber criminal access to your environment or their credentials. The reason phishing is so successful as an attack vector is because they are cheap to craft, easy to deploy to the masses, target people and go right past technical security controls such as firewalls and intrusion detection systems just like any normal email would. This is why it is important to bolster your human firewall by training your users to spot cyber crime associated activities
-
Incident response and disaster recovery plans
Unfortunately, even after preparing well, there is always a possibility of things going wrong. We are seeing an increasing emergence of zero-day attacks. These attacks by definition do not have mitigating controls making them particularly debilitating and hard to defend against. Keeping this in mind, it is wise to have a robust and well-tested incident response and disaster recovery plans. An incident response plan will allow you to respond to a security incident in an effective manner limiting the damage. However, nothing can be guaranteed and this is why a Plan B, disaster recovery plan, is important to allow quick and successful recovery if the attack was to succeed and propagate. Security incidents will happen, but they don’t have to be newsworthy. That’s where robust and well tested incident response and disaster recovery plans come into play.
Taking a methodical approach to cyber security and risk management is likely to result in greater success in defending your organisation against cyber criminals. This article has outlined such an approach centered around the six pillars of cyber security and risk management.





