Phishing is one of the most common and most successful forms of cyberattack: e-mails designed to trick users into providing valuable information (such as login credentials) or running malicious code that compromises their workstation. Unlike other attacks, phishing does not rely on technical vulnerabilities or security misconfigurations to be effective. Instead, phishing preys on ordinary human weaknesses to gain access to sensitive systems or valuable information.
For example, a tired employee sifting through e-mail at the end of a long day may mistake a fabricated IT request or phony retail offer as legitimate, and inadvertently compromise an entire company with one click. Phishing, due to its simplicity and relative ease of deployment, has become a cornerstone attack method for hackers, and one that can have significant repercussions for affected companies.
Phishing is such a potent threat to organisations for several reasons:
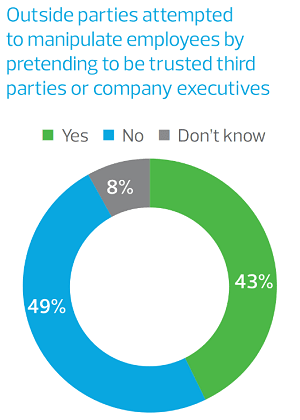
- It’s common. RSM US’s Middle Market Business Index Cybersecurity Special Report research found that 43 percent of executives indicated that outside parties attempted to manipulate their employees into providing access to systems or data by pretending to be trusted third parties or high-ranking company executives.[1]
- It’s effective. On average, 1 in 14 users is successfully tricked into following a link or opening an attachment in a phishing e-mail.[2] When conducting client assessments, we find that phishing continues to be one of the top attack vectors, accounting for 59 per cent of external attacks and 30 per cent of all compromises in 2016.
- It’s costly. Organisations lose money responding to an incident, considering recovering lost data, paying regulatory fines and suffering reputation damage. One report showed that a successful phishing attack could cost the average company $1.6 million.[3]
Aware of these dangers, many companies are taking steps to protect against phishing attacks by conducting awareness training for employees or performing internal phishing campaigns to test their defenses. The central element of a strong phishing awareness training programme is education. You need to know both how to detect a phish and how to properly report it. Therefore, we have reviewed the awareness training programmes at a wide variety of companies to provide you with the most effective methods for protecting yourself and your organisation against this pervasive and persistent risk.
Spotting a Phish
The first step in phishing awareness is recognising the signs of potential phishing. These signs include:
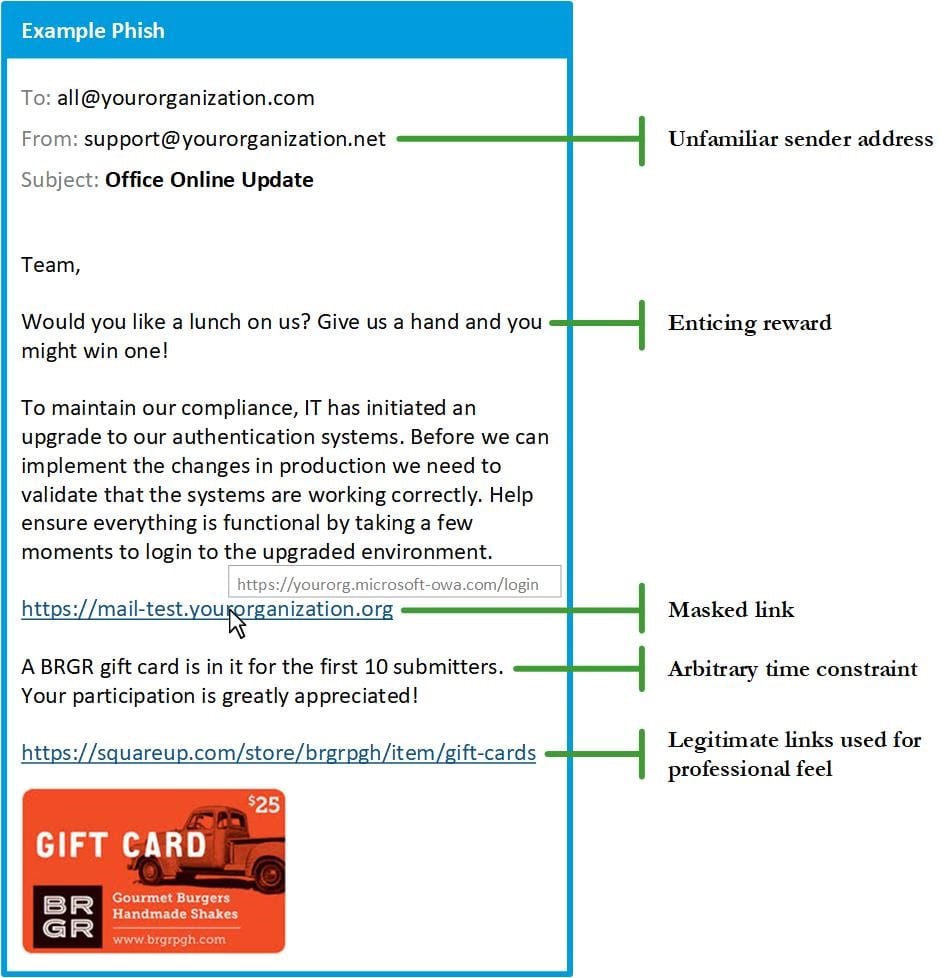
UNFAMILIAR OR MISSPELLED SENDER ADDRESS
Attackers often use false sender addresses, particularly if controls (such as an SPF record) are in place to prevent spoofing from internal addresses. Be on the lookout for addresses ending .corn instead of .com. Also be on the lookout for addresses ending in .net, as well as unusual elements added to the domain such as @example.suspicious.com instead of @example.com.
Tip: When in doubt, Google a suspicious domain name to determine whether it is tied to any known phishing schemes.
UNEXPECTED OR QUESTIONABLE REQUESTS
Any emails asking you to perform an action for which you have had no prior notice (such as upgrading to a new system) should raise alarm bells. Though hackers are tailoring phishes to specific lines of business and using scenarios that people in your organisation may have encountered before, it’s still better to verify with a supervisor before clicking (particularly if the request is completely unexpected).
It’s especially important to be skeptical of emails asking you to authorise major transactions or transfers. Instead, users should verify such actions in person or through channels previously established as legitimate.
MASKED LINKS
Attackers may mask malicious content in a seemingly innocent hyperlink. However, hovering over the link reveals where it will actually send users. Ask yourself: Does the link direct to an unfamiliar site? Does it take you to an unsecured site (HTTP) when it should be directing to a secure site (HTTPS)? Utilising link scanners can also verify a link’s security without having to navigate to the site.
SUSPICIOUS ATTACHMENTS
Many phishing emails are often designed to trick you into downloading a malicious document and enabling macros. Attackers embed macro-based malware in Microsoft Word documents and Excel spreadsheets and design a convincing pretext to convince users to launch the file. Always double check the source of the file and be extremely cautious about enabling macros.
Common Phishing Pretexts
Your users must always be aware of the social engineering techniques that attackers use to try to trick you into performing certain actions.
THREAT
Some of the most convincing phishing e-mails prey on common fears. For example, your Amazon.com account was breached or your e-mail inbox is full and you will not receive new messages. By manufacturing an emergency, these e-mails convince you to act immediately or face serious consequences. As a result, you may be blinded by a threat and in a hurry to fix the supposed problem. This rush may cause you to miss the telltale signs of a phish and inadvertently give up your credentials or download malware. These can be some of the most effective phishing pretexts.

OBLIGATION
More targeted phishing e-mails hinge on your workplace obligations. These e-mails may appear to come from a supervisor or executive asking you to download a document. They may be designed to look like a message from your organisation’s IT or security department, asking you to login to a new site or reset your password. In each case, these phishing attempts are engineered to make you feel as though you must follow the instructions as part of your job. Without proper training or caution, your sense of obligation may override any suspicions you have.
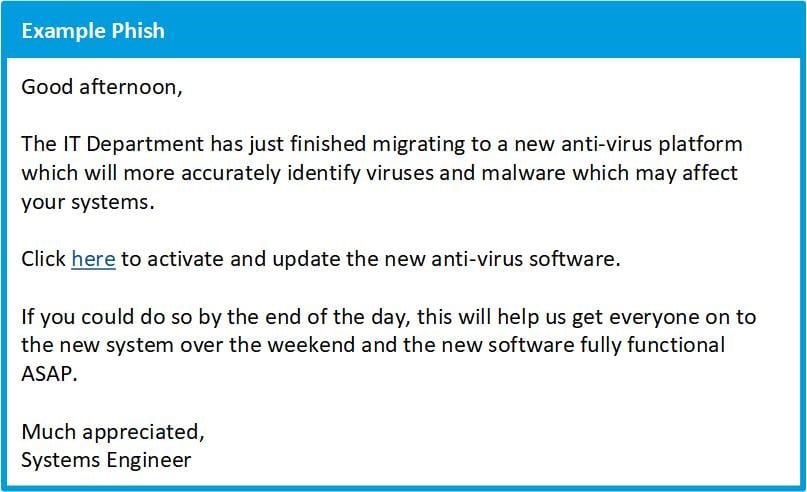
OPPORTUNITY
Many phishing e-mails offer an enticing opportunity in the hope to lure you into performing a specific action. For example, an e-mail may be designed to look like coupon, contest or company appreciation effort with various potential rewards. Attackers will use almost anything as bait: a gift card to a grocery store or restaurant, tickets to a local sports event, or just plain old cash. If the right opportunity comes along and you’re not careful, you might get phished.

Reporting a Phish
In the rush to reduce risk, it can be easy to focus entirely on phishing detection and forget the second step: reporting. Many organisations hope that regular awareness training will reduce user click rates to zero. However, eliminating failures entirely is not a realistic goal. Even a well-trained employee can fall for a carefully crafted phish at the end of a long day. For that reason, it is just as important to learn how to report an e-mail phish as well as who to report it to. By improving response time with a strong reporting procedure, you can reduce or eliminate the damage of even a successful phish.
Take the following actions when spotting a phish:
- Immediately inform a manager or supervisor.
- Record the incident via a help-desk ticket or e-mail to security or IT personnel (depending on your organisation). This will create a paper trail, which can be important to the incident response or disaster recovery plan. It also sets the wheels in motion for a full security response.
- Do not forward the e-mail to anyone, even when reporting the incident. This only acts to spread the risk, increasing the chances that another user may inadvertently click on a malicious link or attachment.
- If necessary, take a screenshot of the e-mail to capture the relevant information.
At this point, your organisation’s security or IT team can respond to the incident by:
- Alerting users of the phish
- Recalling the e-mail from user inboxes to prevent further damage
- Blocking the IP address of the attacker
- Examining potentially compromised devices or systems
- Investigating what further access the attacker may have gained
- Changing passwords as necessary
These processes should be outlined in your incident response policy. The clearer the reporting and incident response policy, the faster your organisation will be able to block attacks.
Spread the Word
 Protecting against phishing attacks is a group effort. The more employees can educate themselves and others on how to spot and report phishing attempts the safer everyone will be.
Protecting against phishing attacks is a group effort. The more employees can educate themselves and others on how to spot and report phishing attempts the safer everyone will be.
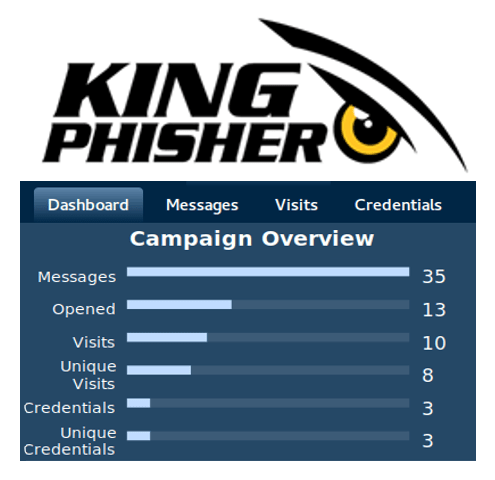
Organisations looking to do more can conduct quarterly phishing assessments to test users and identify areas for improvement. In addition, some automated tools are available to test your organisation’s vulnerability to and preparedness for inevitable phishing attacks. For example, RSM offers a free, open source tool called King Phisher that enables you to test your own susceptibility to phishing by sending a sample phishing e-mail to your team and tracking user responses.
King Phisher allows you to select sample phishing e-mails or design your own customised phishes aligned to your organisation’s training plan. For instance, after a lesson on common phishing pretexts, you can send users a similar phish to test their awareness and reinforce the specific training. Like anything else, the more you practise the better you will become at catching phishing attempts.
By learning how to detect and respond to a phishing attack, you can become the first line of defense in your organisation’s security program.
END NOTES
- It’s common. RSM US’s Middle Market Business Index Cybersecurity Special Report research found that 43 per cent of executives indicated that outside parties attempted to manipulate their employees into providing access to systems or data by pretending to be trusted third parties or high-ranking company executives.[1]
- It’s effective. On average, 1 in 14 users is successfully tricked into following a link or opening an attachment in a phishing e-mail.[2] When conducting client assessments, we find that phishing continues to be one of the top attack vectors, accounting for 59 per cent of external attacks and 30 per cent of all compromises in 2016.
- It’s costly. Organisations lose money responding to an incident, considering recovering lost data, paying regulatory fines and suffering reputation damage. One report showed that a successful phishing attack could cost the average company $1.6 million.[3]
Original source: https://www.rsm.global/kenya/insights/consulting-insights/phishing-awareness-recognizing-addressing-and-avoiding-threats

