AUTHORS

In today's interconnected digital landscape, safeguarding sensitive data and fortifying cyber security defences have become paramount.
Enter the world of ethical hacking and penetration testing, a dynamic and strategic approach that serves as a robust protection against cyber threats. Join me as we delve into the art of ethical hacking, exploring the fascinating realm of penetration testing and its pivotal role in bolstering digital resilience.
Unveiling the Ethical Hacker's Canvas
Ethical hacking, often referred to as penetration testing or pen testing, is the practice of simulating real-world cyberattacks on systems, networks, and applications to identify vulnerabilities before malicious actors can exploit them. The primary goal is to proactively strengthen security measures and ensure that organisations stay one step ahead of potential threats.
Mastering the Craft
Ethical hackers, equipped with an arsenal of cutting-edge tools and a deep understanding of cybersecurity principles, embark on a mission to mimic the tactics, techniques, and procedures (TTPs) employed by cybercriminals. By mirroring the actions of adversaries, ethical hackers uncover vulnerabilities, assess potential risks, and provide actionable recommendations for mitigation.
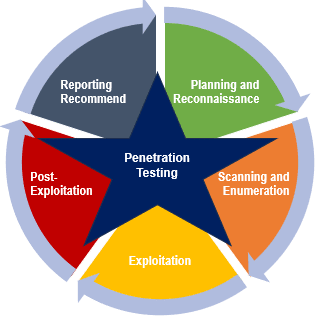
The Penetration Testing Lifecycle
A successful penetration test consists of a well-defined lifecycle, similar to a strategic game of chess. From reconnaissance and vulnerability analysis to exploitation and reporting, each phase contributes to a comprehensive assessment of an organisation's security posture.
- Planning and Reconnaissance: Ethical hackers gather intelligence about the in-scope target, understanding the organisation's digital footprint, domain structure, and potential entry points.
- Scanning and Enumeration: Tools are wielded to scan for vulnerabilities and enumerate assets, identifying potential weak spots ripe for exploitation.

- Exploitation: With a deepened understanding of the target, ethical hackers attempt to exploit vulnerabilities to determine the true risk of the vulnerability and establish that a real vulnerability exists.
- Post-Exploitation: Ethical hackers try to escalate the privileges and gather sensitive artifacts and data focussed on an analysis of the identified vulnerabilities, including identifying potential root causes.
- Reporting and Recommendation: The findings are meticulously documented, vulnerabilities ranked by severity, and recommendations provided to secure defences.
Elevating Cyber Resilience
The significance of penetration testing lies not only in its ability to identify vulnerabilities, but also in its potential to elevate an organisation's overall cyber resilience. With a proactive approach to security, organisations can pre-emptively address weaknesses, implement robust security measures, and prevent potential breaches before they occur.
As we navigate the evolving landscape of cyber threats, ethical hacking emerges as a formidable ally. It empowers us to anticipate and counteract potential risks, safeguarding data integrity, privacy, and organisational reputation. Join the league of ethical hackers and be part of a transformative journey that reshapes the future of cyber security.
FOR MORE INFORMATION
If you would like to learn more about the topics discussed in this article, please get in touch with our Security & Privacy Services.