The recent major cyberattack on SingHealth’s database that resulted in the theft of some 1.5 million patients’ personal particulars is another wake-up call for organisations to be vigilant for cyber risks. The repercussions may be more serious than you think.
SingHealth sent out the following two short messages to victims of the cyberattack:
- “-your name, IC, address, gender, race, birth date & outpatient dispensed medicines in 2015-18 were accessed but not altered. Mobile no., medical & financial info unaffected. No action needed. We apologise for anxiety caused. For queries 6326-5555 (9am-9pm)”
- “-your name, IC, address, gender, race & birth date were accessed but not altered. Mobile no., medical & financial info unaffected. No action needed. We apologise for anxiety caused. For queries [email protected]”
It is clear that information such as the National Registration Identity Card (NRIC) number, address, birth date and mobile number are often required for identification in many facilities and services that we use.
In the wake of this latest attack, it is timely to alert your staff to take the following precautions, regardless if their data has been accessed or not:
- Be aware of phishing emails, fake SMSs and calls since cyber attackers already have your personal information such as the birth date, mobile number and address.
- Set the threshold limit to the minimum (e.g., a dollar for OCBC users) in iBanking and other bank transactions, so that SMS alerts can be triggered.
- Always choose iBanking over phone transactions as banks use two-factor authentication, which requires a one-time PIN or code from the mobile device or security token to authorise any transaction. Phone banking can be carried out by attackers posing as targets to perform transactions, as banks may be using simpler authentication procedures that only require the birth date, mobile number and address to confirm identities.
- Inform the Cyber Security Agency of Singapore (CSA) or police of any suspicious activities.
On 20 July 2018, Channel NewsAsia reported that “CSA ascertained the cyber attackers first accessed the network after breaching a front-end workstation, and managed to get privileged access to the database over time while also showing sophistication in cleaning up their digital footprints when doing so.”
Is “breaching a front-end workstation” that simple? The answer is “yes” and it is always the single point of entry, not the single point of failure that creates another wake-up call for everybody.
In another case in 2016, TODAY reported the following: “One receptionist used a single-letter password to access the company system, and on one occasion, K Box Entertainment Group received more than 90,000 members’ personal data, unencrypted, via Gmail from its IT vendor, Finantech.”
It is indeed easy for an intruder to walk past a sleeping or inattentive security guard to access a building. Once inside, it is easy to wait for an opportunity to closely follow an employee into the office. In the office, it is easy to walk around to identify which rooms are unlocked without being challenged or questioned by non-vigilant staff. It is not difficult to monitor different activities in the office and leave when the office closes. If the intruder fails to gain entry at any point without being caught, he can always try again the next day. It would only be a matter of time before his persistence pays off.
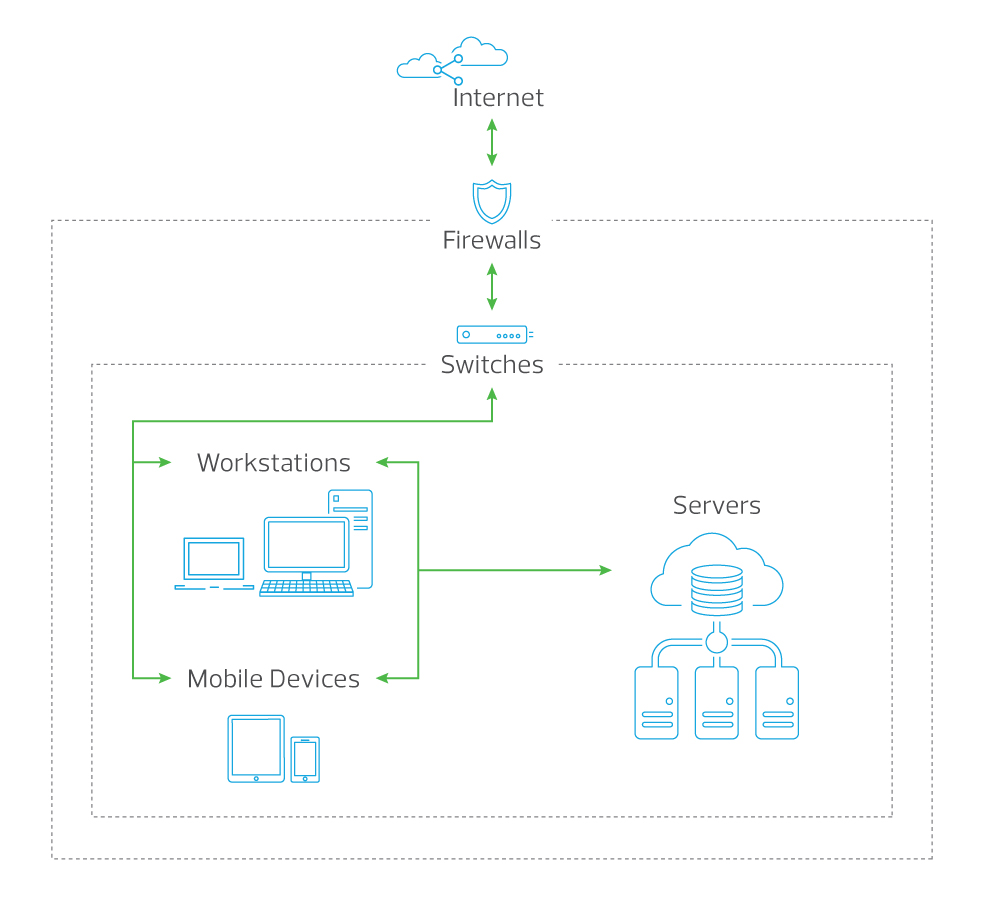
Our walls may be strong enough to prevent unauthorised access, just as our firewalls and switches might be able to protect the organisation from external attacks. Cyber attackers know this and can get into your network from the inside through social engineering attacks. It is simple for an employee to click on a seemingly harmless web link, download a file from the internet, visit a malicious website or use an infected USB drive. All these are easy access channels for cyber attackers. Workstations and mobile devices are common targets as they connect the internal and external networks.
Taking the recent SingHealth breach as an example, informing 1.5 million users via SMS would cost about $150,000, excluding expenses such as setting up the website for users to check the status, internal/external investigations, internal/external communications, crisis management, stopgap solutions, and recovery. The costs of damage and recovery are enormous.
Organisations are strongly encouraged to review their systems and be vigilant for suspicious activities to mitigate their risk of becoming the next victim. They should adopt the following measures immediately as recommended by CSA:
- Harden standard workstations and endpoints
- Review administrator accounts
- Disable PowerShell for standard workstations
- Tighten control for long-running or decommissioned endpoints
- Implement strong endpoint protection
- Keep systems up-to-date
- Monitor for unauthorised remote or database access
Minimise your exposure to cyberattacks. Contact us for a cybersecurity review.



