Introduction
Real estate and construction (REC) has been perceived as a traditional industry. However, hackers do not discriminate and the REC industry is a tempting target with access to both confidential client data and regular payment streams. But is the industry sufficiently aware of and protected against cyberthreats in an increasingly digitised work environment?
The true scale of the problem is difficult to estimate. As businesses may be reluctant to publicise their cybersecurity failings, only a small number of attacks are revealed. In this article, we will highlight the types of data stolen from REC businesses and discuss how to step up cybersecurity initiatives in response to these threats.
What are the types of data stolen from REC businesses?
Building blueprints
This is indeed the worst nightmare for many REC businesses and clients. For example, the blueprints of the new Australian intelligence service’s HQ were stolen in 2013. The attack took place through the computers of an unnamed construction contractor, exposing floor plans and locations of communications cabling, servers and security systems. As hackers gained access to such sensitive information, huge potential liabilities and cost overrun issues are likely to follow. This incident also prompted debate on whether governments should impose mandatory data breach disclosure laws on organisations that had a data breach.
Personal Identifiable Information (PII)
Many REC businesses have significant amounts of PII about customers and tenants contained in leases and rental applications. Such sensitive data may be vulnerable to cybercriminals masquerading as a colleague or a partner. Such attacks are known as “spear phishing” and typically involve fake emails sent from seemingly legitimate accounts. Turner Construction in the US was the victim of a spear phishing scam in 2016 when an employee sent tax information on current and former employees to a fraudulent email account. In this case, the cybercriminal may be seeking such information to engage in identity theft.
Cash
In 2015, up to €17.2 million was stolen from one of the foreign subsidiaries of Finnish crane-maker Konecranes. This company indicated that the perpetrators used identity theft and other means to induce the subsidiary to make unwarranted payments. This highlights the threat of identity theft where stolen identities are “monetised” through fraudulent transactions. Commendably, Konecranes released a public announcement on this matter to educate other businesses.
Which part of IT systems/infrastructure do breaches commonly occur?
Personal devices
As digital technologies become more widespread, data is transmitted to multiple channels that may include non-office environments such as email on mobile devices. Personal mobile devices are particularly susceptible to data leaks because they can be lost or stolen, as well as more easily accessed by cybercriminals.
More worryingly, according to a public awareness survey by the Cyber Security Agency of Singapore (CSA) in 2017, over a third of respondents delayed installing software updates on their mobile devices (see chart below). This leaves users vulnerable in the interim and is bad news for REC businesses seeking the cooperation of their employees to install the latest email security patches.
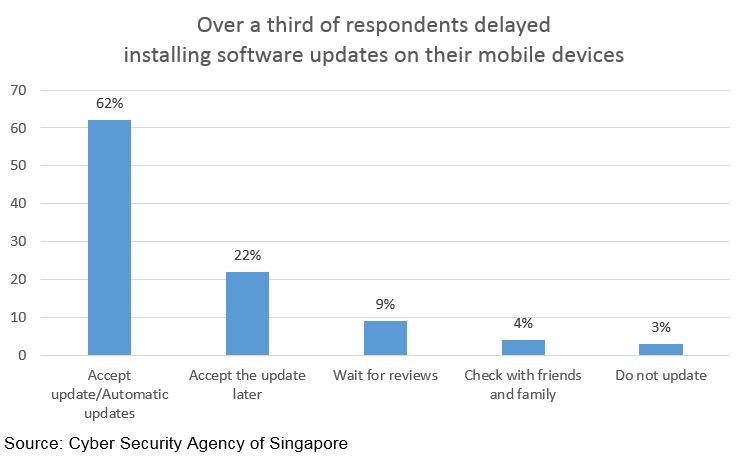
Password-related failures
According to the aforementioned CSA survey, many respondents had lax password management practices (see chart below). 30% of the respondents used the same password for work and personal accounts. Therefore, a compromised personal account may lead to a similar problem for a work account if hackers can connect the dots using social media profiles or other publicly available information.
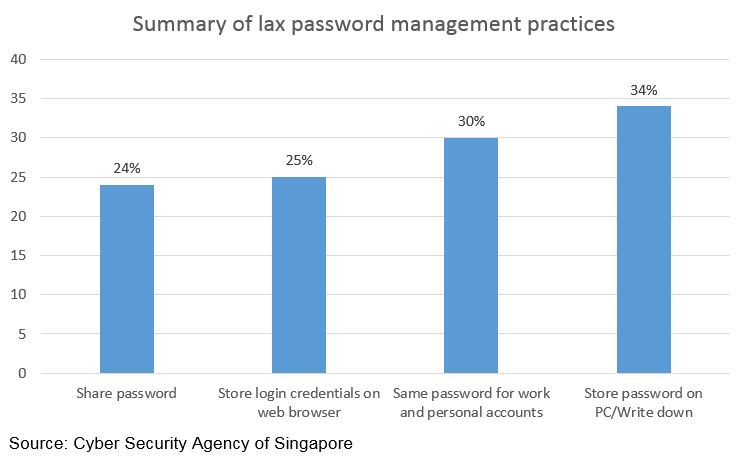
Computer/Network
As REC businesses increasingly integrate smart technologies and devices into building management systems — power, heating, ventilation and air conditioning (HVAC), lighting, smart thermostats — hackers have additional opportunities to breach these systems.
For example, Target, a large US retailer, suffered a credit and debit card data breach that affected 110 million accounts in 2014. These cybercriminals stole credentials from Target’s HVAC provider and eventually gained access to the sensitive data.
Steps that REC businesses can take to review their cybersecurity
At this point, we seek to answer the most important question: “What can businesses do to protect themselves?” We have compiled a list of steps that any REC business can take to review and enhance its cybersecurity.
Review password policies
As a business, it is prudent to review your existing policies and ensure that employees define a secure password for your systems. Unnecessary risks, such as a one-letter password or a password that never expires, should be avoided at all costs.
Review domain and network security
You can’t manage what you can’t track — this principle applies to cybersecurity as well. By tracking user devices and mapping them to specific switch ports, your business will be better prepared to detect any suspicious activities for swift investigation and rectification.
Review the frequency of patching
Cybersecurity has sometimes been described as an arms race between the good and bad guys. You should review the frequency of patching and ensure that a framework is in place to keep every device (work computers, point-of-sale systems, mobile devices) updated during these regular exercises.
Review employee awareness
Cybersecurity breaches often start with a single point of failure that could have been avoided, such as spear phishing. Your business needs to review whether employees have been educated about the top cybersecurity risks and ensure that clear policies as well as procedures are developed.
Review procedures through the eyes of a ‘hacker’
This is the cybersecurity equivalent of a fire drill. In particular, REC-specific vulnerabilities, such as building management systems (BMS), should be examined. Hopefully, this exercise will weed out glaring mistakes that hostile actors can take advantage of. For example, IBM UK’s ethical hacking team exploited a BMS with a weak password to access a client’s main computer system and demonstrate that data records were vulnerable.
Conclusion
As stated in our earlier article, the costs of damage and recovery after a cyberattack are enormous as seen from SingHealth’s recent cyber breach incident announced in July 2018. We had estimated that just informing 1.5 million users via SMS would cost about $150,000.
With such high financial and reputational risks, it is no wonder that REC businesses are actively seeking to enhance their cybersecurity. But taking the first few steps may be difficult as few are aware of where and how to begin. Building and maintaining these capabilities in-house may not be cost-effective for smaller businesses. Therefore, more businesses are outsourcing this function to managed service providers to gain an added layer of cyber protection at a fraction of the time, effort and cost.
We pride ourselves in helping businesses to set up effective defences against cyberattacks to ensure business continuity. Contact us for a complimentary disaster recovery review to determine your business’ level of readiness in the event of a cyberattack or incident.

